Malware analysis report: WinDealer (LuoYu Threat Group)
WinDealer is a type of malware that is used for financial fraud and theft. It is a banking Trojan that is designed to steal sensitive financial information, such as login credentials, credit card numbers, and other personal information from victims’ computers.
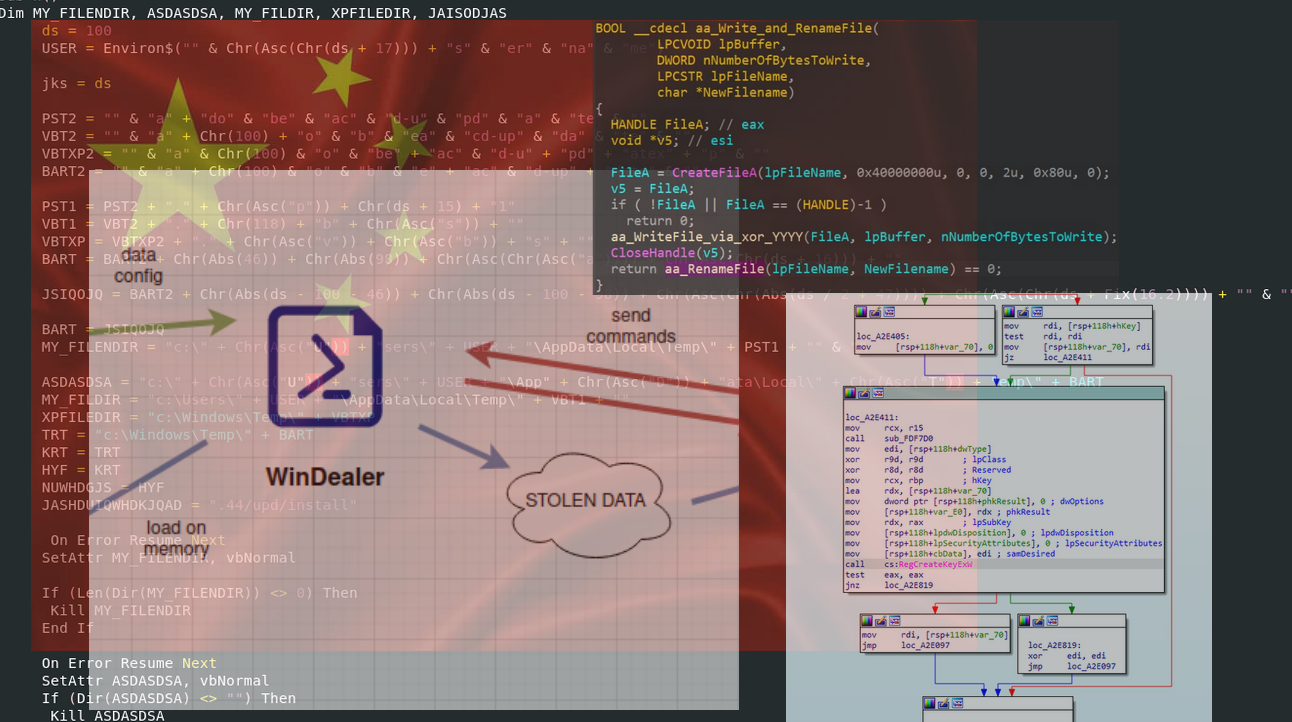
Following are the capabilities of the malware:
- Manipulation of files and file systems: reading, writing, and deleting files, listing directories, and collecting disk information
- Information collection: gathering device details, network settings, and/or keyboard layout, listing running processes, installed software, and configuration files of popular messaging services (Skype, QQ, WeChat, and Wangwang);
- Download and upload random file types; arbitrarily executed commands;
- System-wide text file and Microsoft Word document search;
- Screenshot taking;
- Discovery of networks through ping scan;
- Backdoor maintenance: enabling or disabling persistence (through the RUN key in the registry) and configuration changes
Threat actor
LuoYu is a threat group that is believed to be a Chinese state-sponsored hacking group. The group has been active since at least 2011 and is known to target a wide range of industries, including defense, government, telecommunications, and technology.
Target
Geographies and sectors:
- Chinese subsidiaries of Japanese companies
- Users of a Chinese private bank
Industry:
- Technology
- Media
- Financial
- Military
- Telecom
- Ministries of Foreign Affairs
Cyber Kill Chain
WinDealer steals information of an infected PC and sends it to a C2 server as described in here:
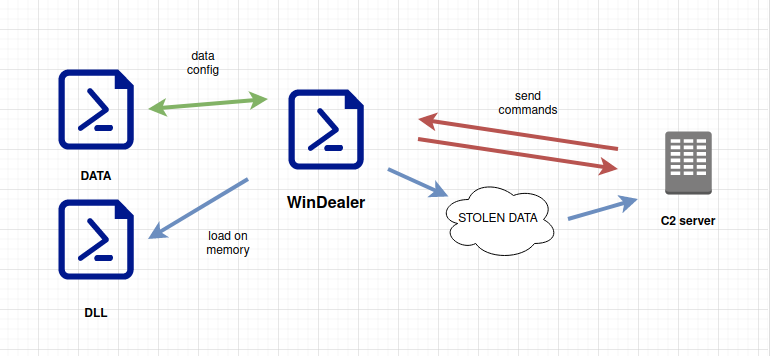
Identification
Two samples are being investigated:
sample.exe:
File size: 372736 bytes
MD5 sum: cc7207f09a6fe41c71626ad4d3f127ce
SHA-1 sum: 84e749c37978f9387e16fab29c7b1b291be93a63
SHA-256 sum: 28df5c75a2f78120ff96d4a72a3c23cee97c9b46c96410cf591af38cb4aed0fa
First of all, check our sample via VirusTotal:
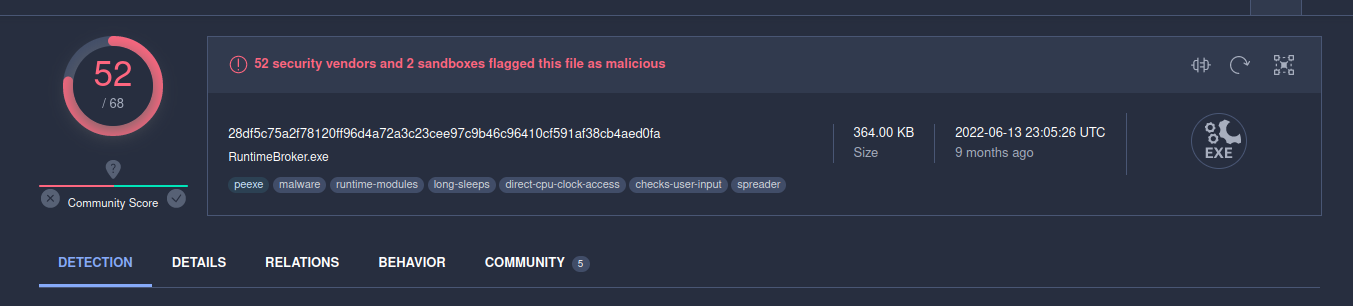
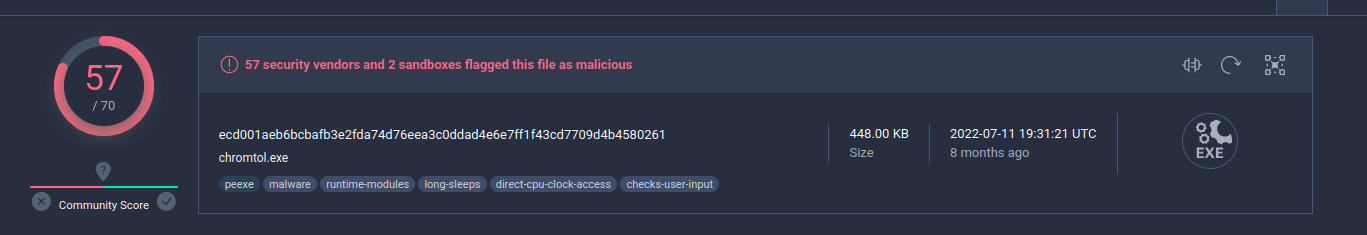
So, 52 of 68 AV engines detect our sample as malicious.
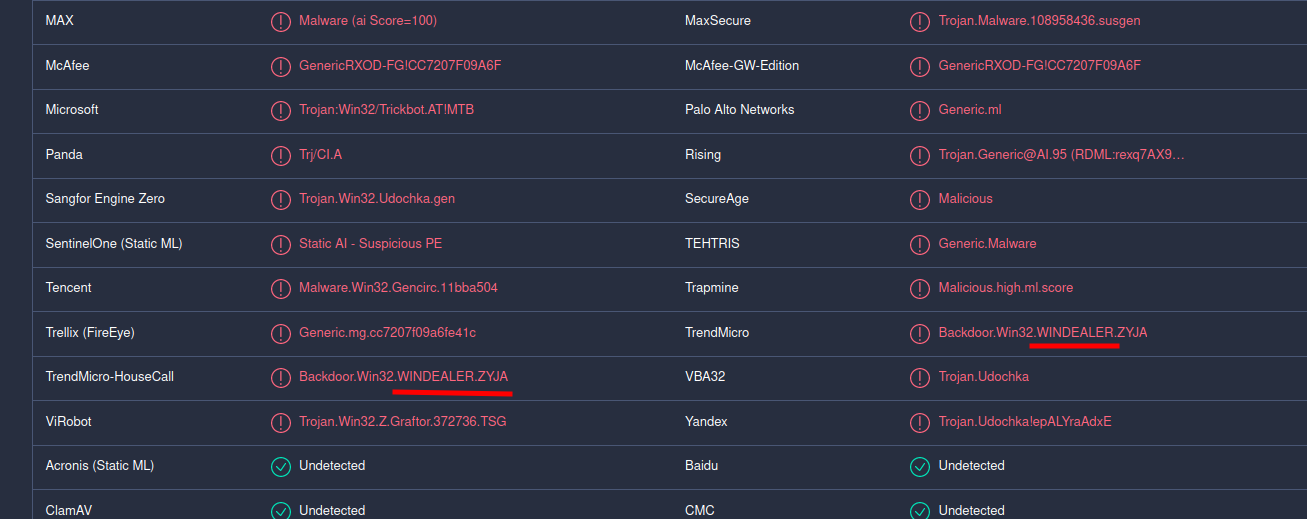
More of them detect file as Backdoor.Win32.WINDEALER.ZYJA.
Static analysis
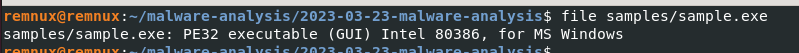
The specified sample is a PE file:
file <sample.exe>
hexdump -C <sample.exe>
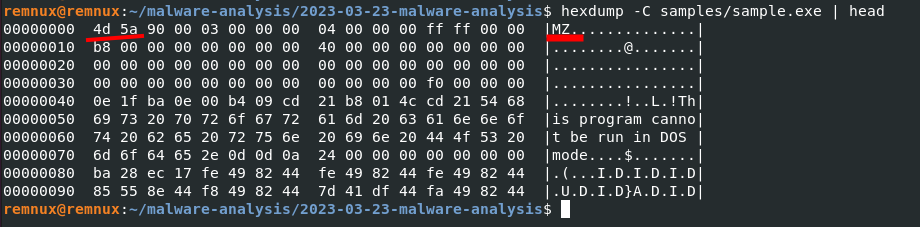
Use exiftool for looking metadata:
exiftool <sample.exe>
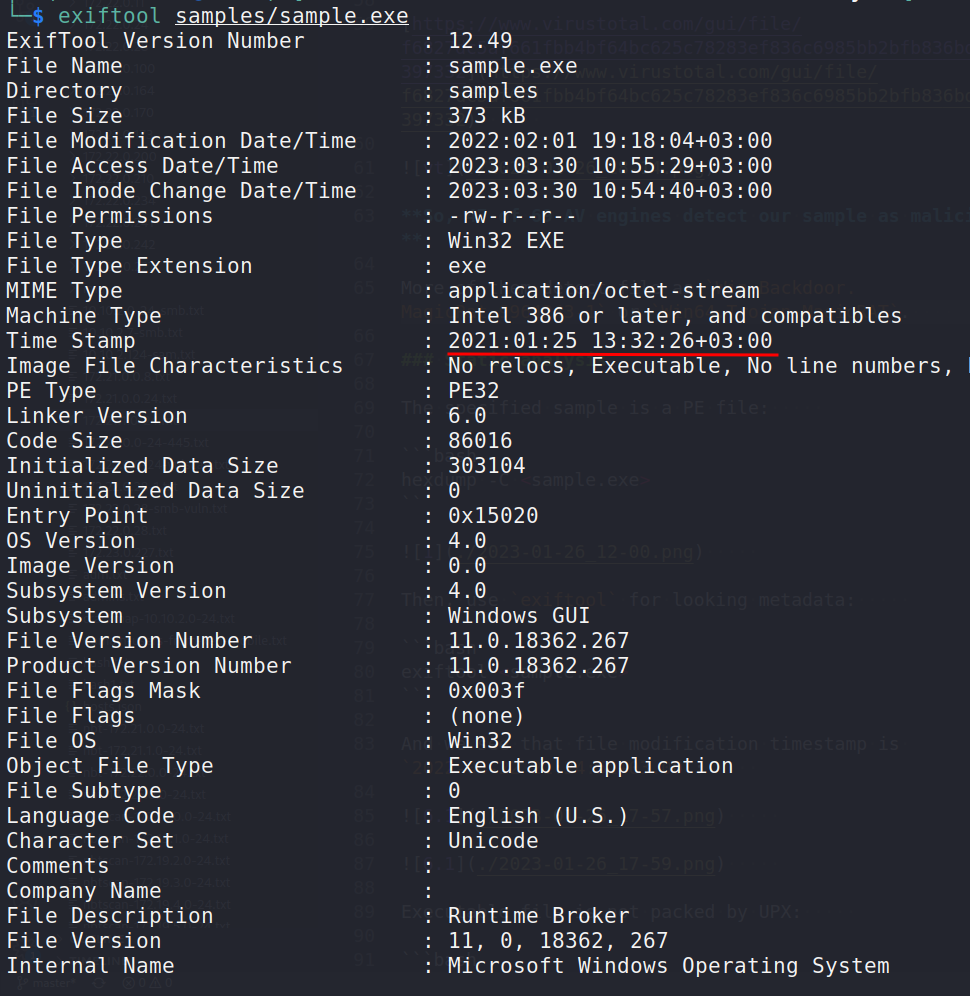
And we see that file timestamp is 2021-01-25 13:32:26+03.00
Executable sample is not packed by upx:
upx -l <sample.exe>
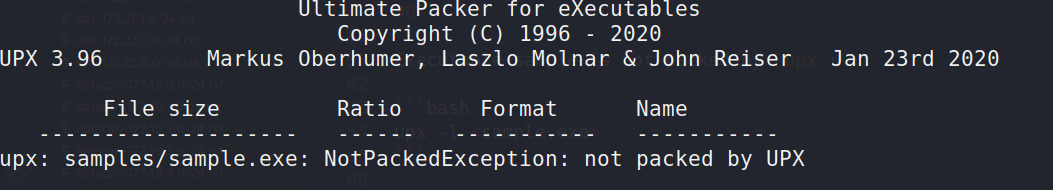
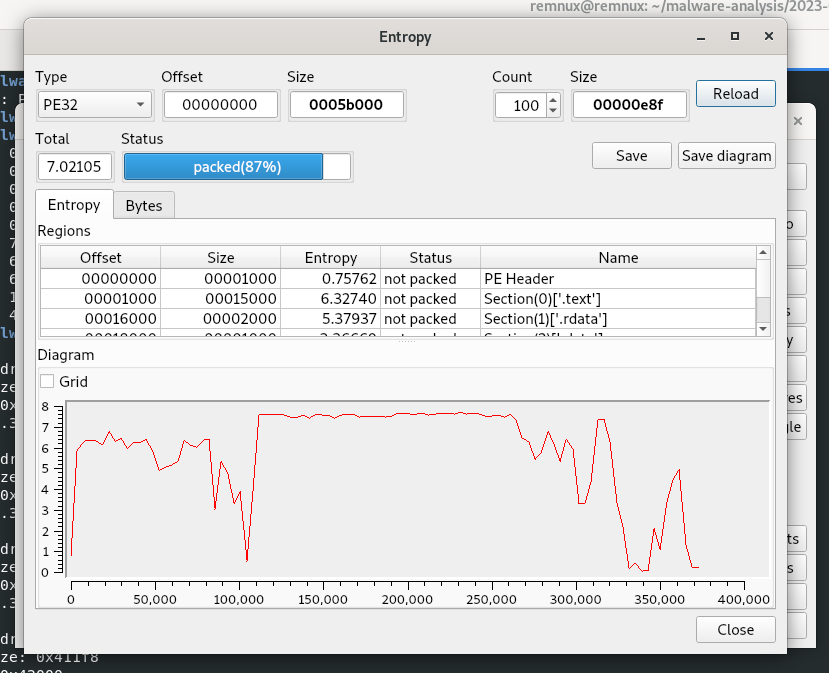
What about Shannon entropy of the sample:
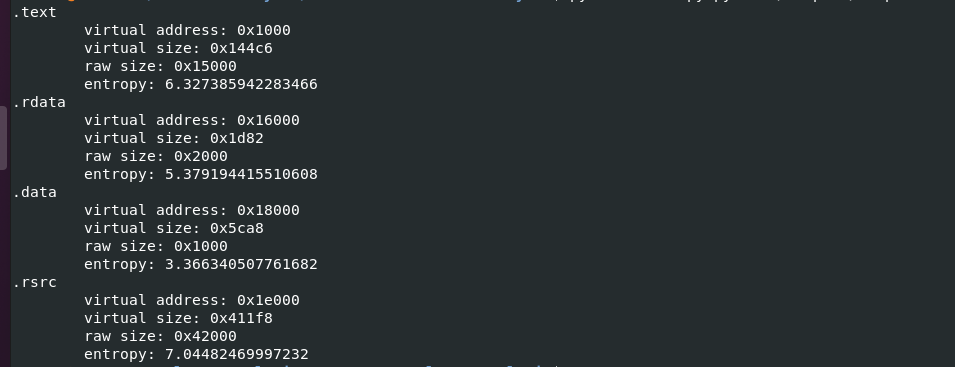
Analysze with DIE says that the compiler is Microsoft Visual Studio C++ (6.0):
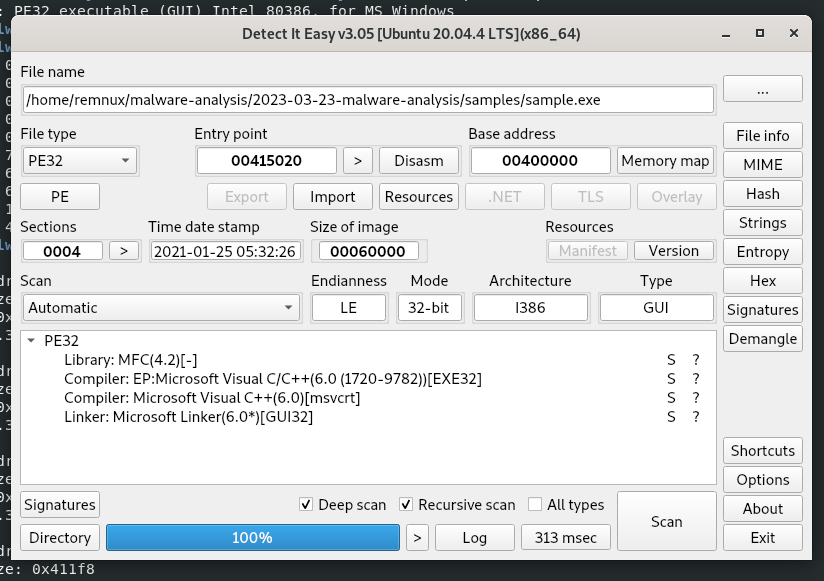
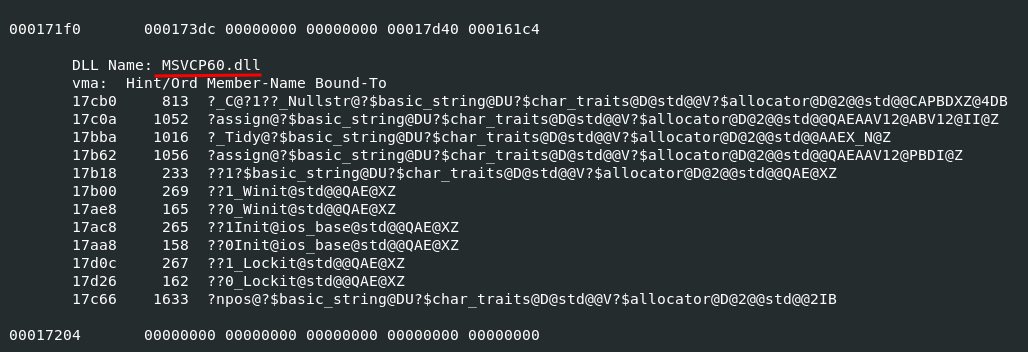
Malware contains encrypted DLL:
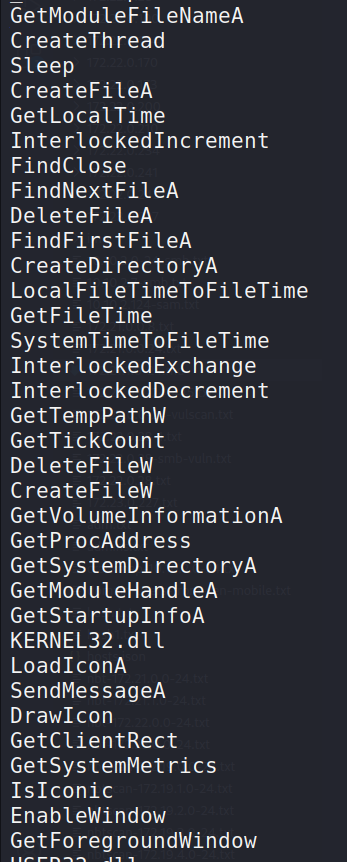
Interesting strings:
The hardcoded version of WinDealer:
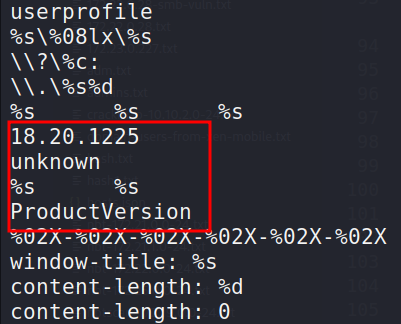
18.20.1225 - version: 18, year: 2020, month and day: 12.25
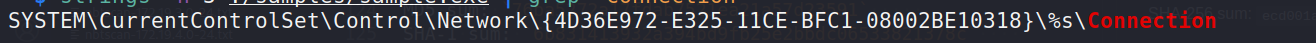
another intersting strings is:
SYSTEM\CurrentControlSet\Control\Network\{4D36E972-E325-11CE-BFC1-08002BE10318}\%s\Connection:
Dynamic analysis
The sample is GUI application:
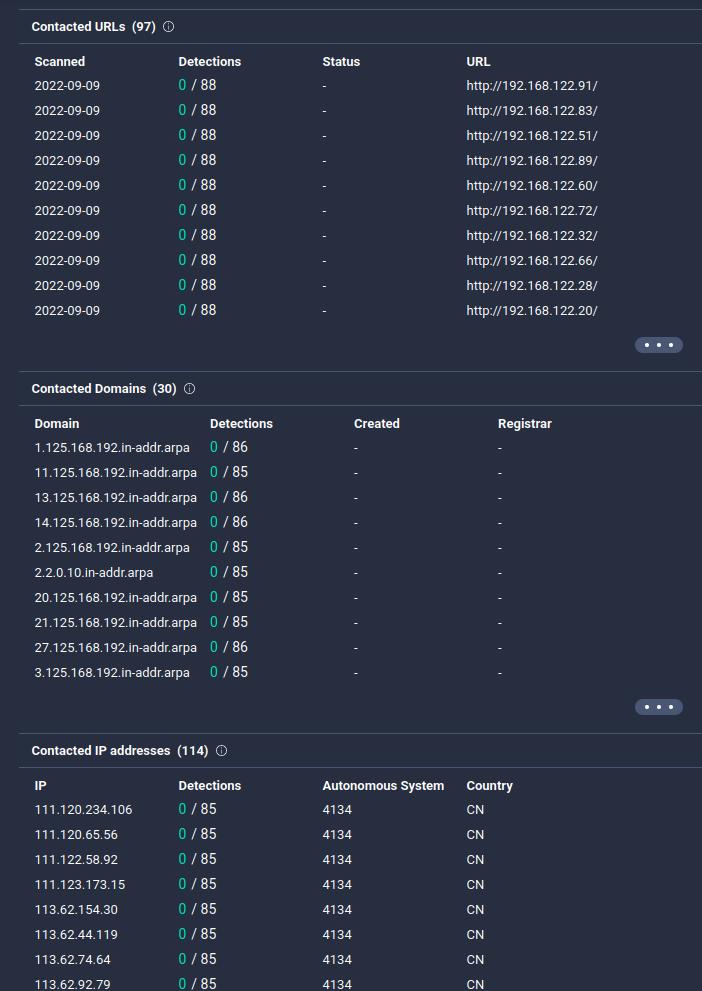
Contacted IP addresses is:
May sleep (evasive loops) to hinder dynamic analysis:
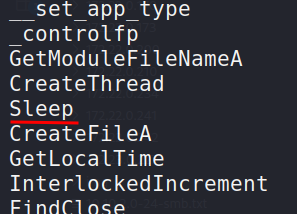
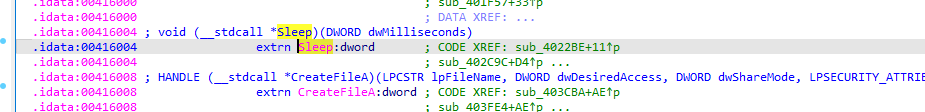
The operator has the power to rename, move, and delete files on the target machine:
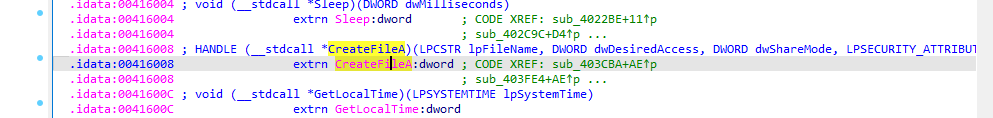
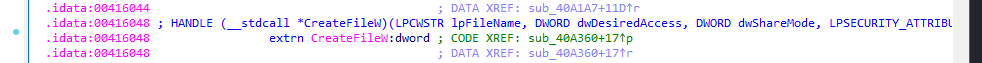
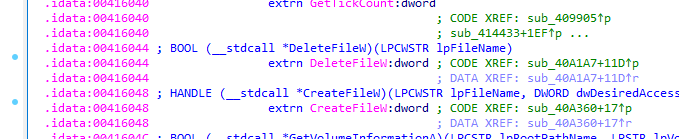
Also malware search through directories and enum filesystem:
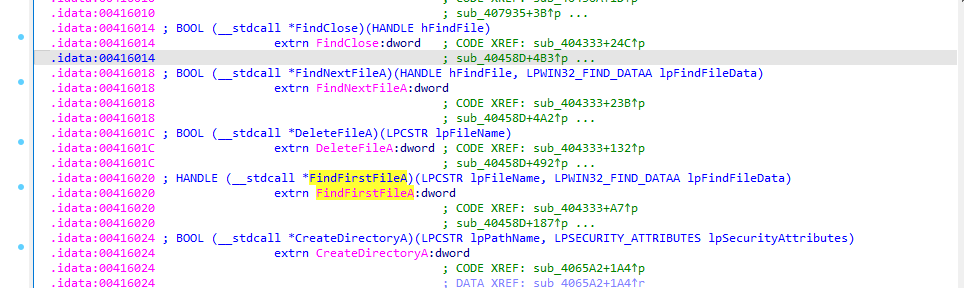
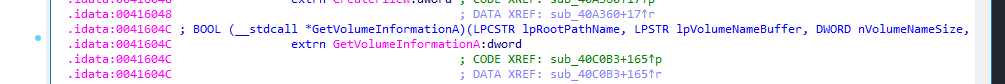
and collecting volume information:
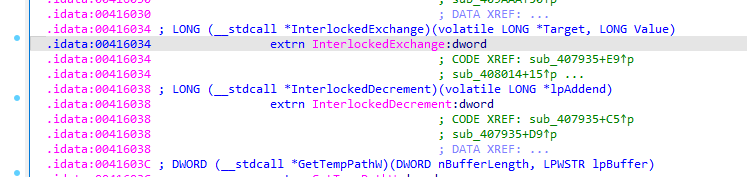
API hooking
Using InterlockedExchange, probably the malware sample is hooking the winapi functions:
AV/Sandbox evasion
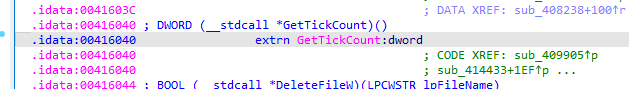
In the malware sample above, the delay timeout is set using the GetTickCount() timer function. The Sleep() function is called in a loop until the timer timeout. In the sandbox, delays that are performed by the Sleep() function are skipped (replaced with a very short timeout) and the virtually elapsed time will be much higher than the requested timeout. The concept behind these methods is to measure elapsed time while running several forms of delays in parallel:
sample2.exe:
File size: 458752 bytes
MD5 sum: 76ba5272a17fdab7521ea21a57d23591
SHA-1 sum: 6b831413932a394bd9fb25e2bbdc06533821378c
SHA-256 sum: ecd001aeb6bcbafb3e2fda74d76eea3c0ddad4e6e7ff1f43cd7709d4b4580261
VirusTotal scan result:
Static analysis
The specified sample is a PE file:
file <sample2.exe>
hexdump -C <sample2.exe>
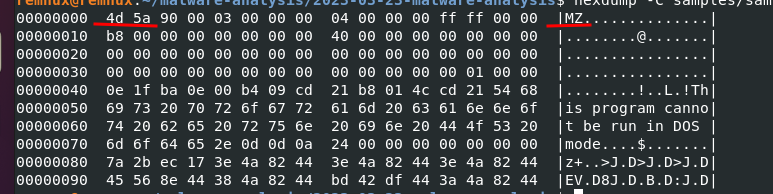
Run exiftool for extracting metadata:
exiftool <sample2.exe>
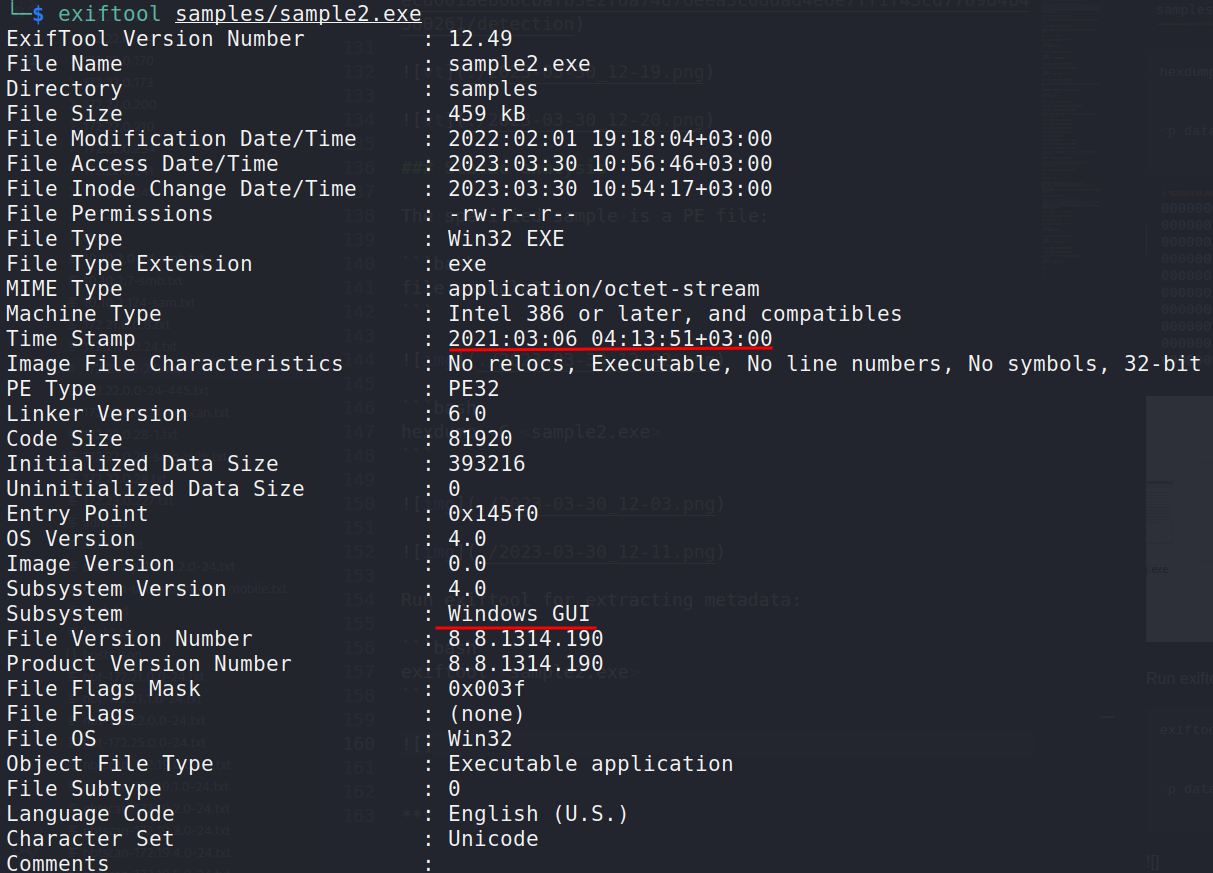
The sample is a Windows GUI file with timestamp: 2021:03:06 04:13:51+03:00
Dynamic analysis
Generating victim ID set in a registry key:

The format of the victim ID is md5("<MAC address>+<Physical_Drive_info>+<username>"). The malware generates a unique registry entry to store the victim ID for subsequent execution. The victim ID is not saved as raw data; instead, the malware changes the 4 bytes victim ID to an IP address format.
This sample collecting host information:
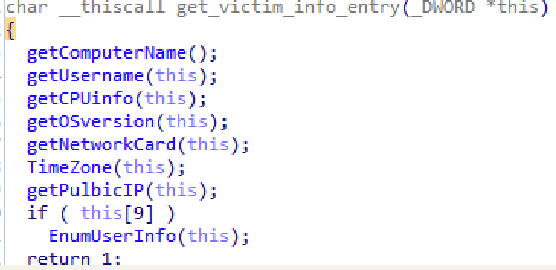
Encoding
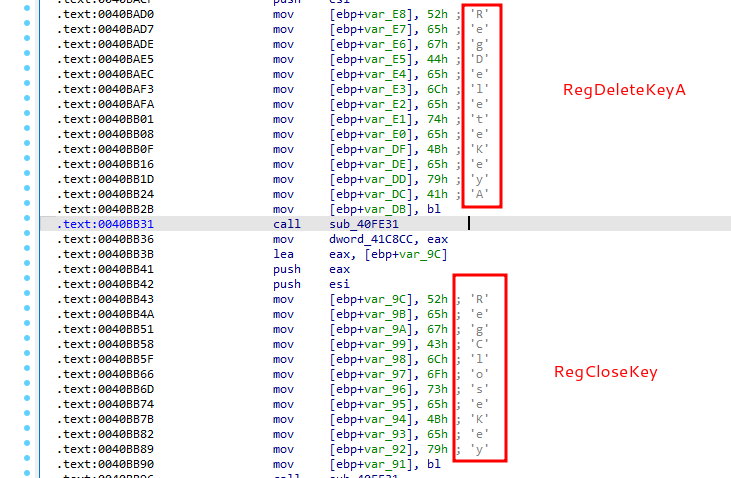
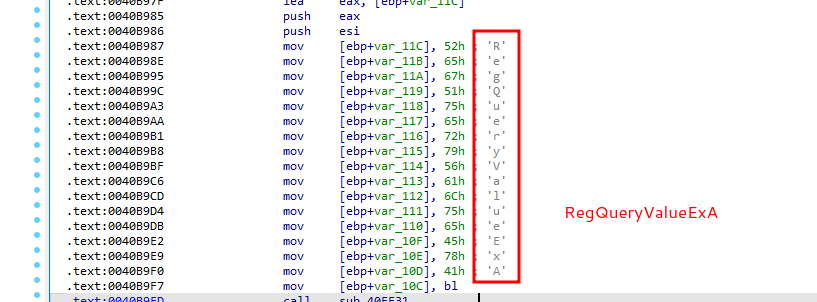
Malware sample use function call obfuscation:
GetUserNameW:
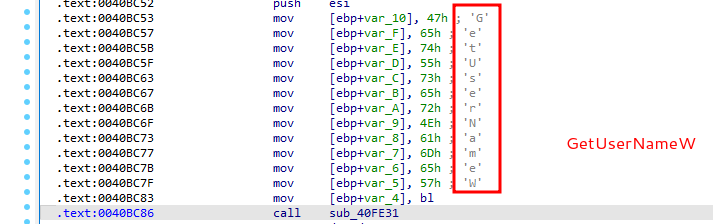
RegCreateKeyExA:
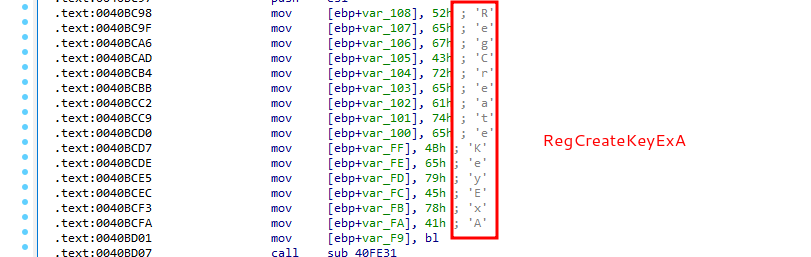
RegDeleteKeyA and RegCloseKey:
RegQueryValueExA:
GetTokenInformation:
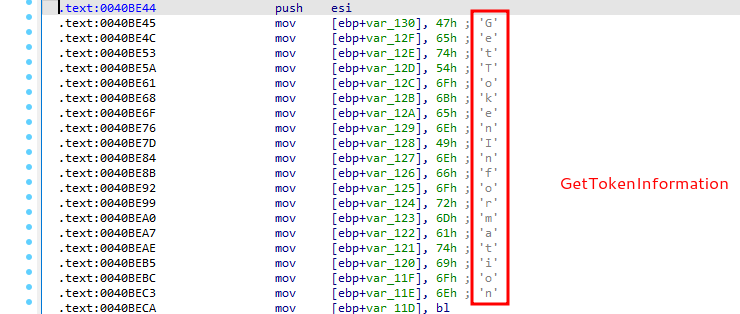
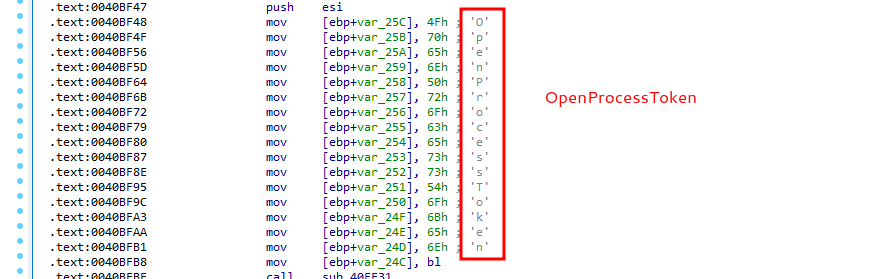
OpenProcessToken:
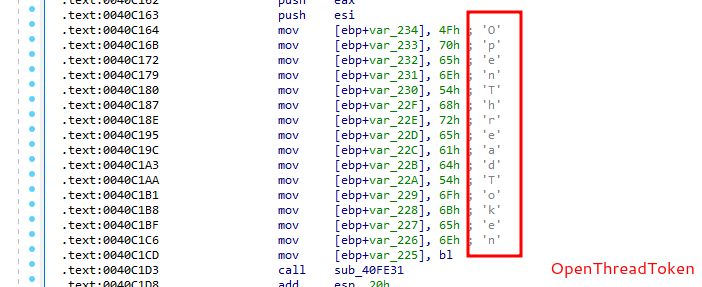
OpenThreadToken:
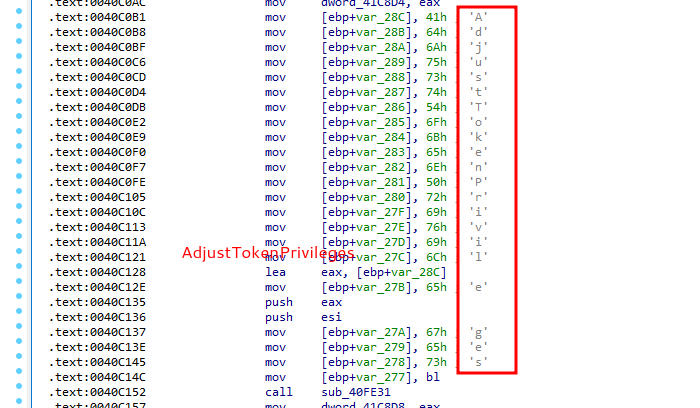
AdjustTokenPrivileges:
.etc.
So, malware sample use one of the interesting classic APT techniques: Token theft via turn on SeDebugPrivilege:
//....
HANDLE token;
TOKEN_PRIVILEGES tp;
LUID luid;
BOOL res = TRUE;
tp.PrivilegeCount = 1;
tp.Privileges[0].Luid = luid;
tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;
if (!LookupPrivilegeValue(NULL, priv, &luid)) res = FALSE;
if (!OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES, &token)) res = FALSE;
if (!AdjustTokenPrivileges(token, FALSE, &tp, sizeof(TOKEN_PRIVILEGES), (PTOKEN_PRIVILEGES)NULL, (PDWORD)NULL)) res = FALSE;
//...
Registry Modifications and Persistence
With a high degree of probability, it can be argued that WinDealer has the functionality of interacting with the registry, probably for persistence mechanism:
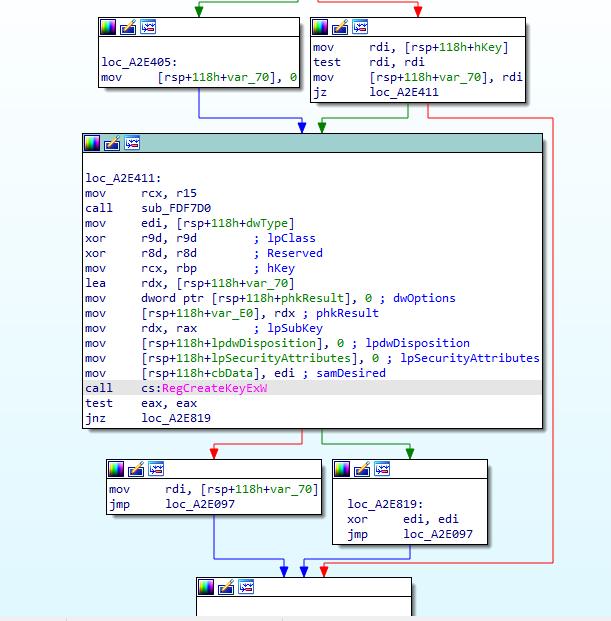
Encryption
Generate 16 bytes AES key to encrypt C2 communication:
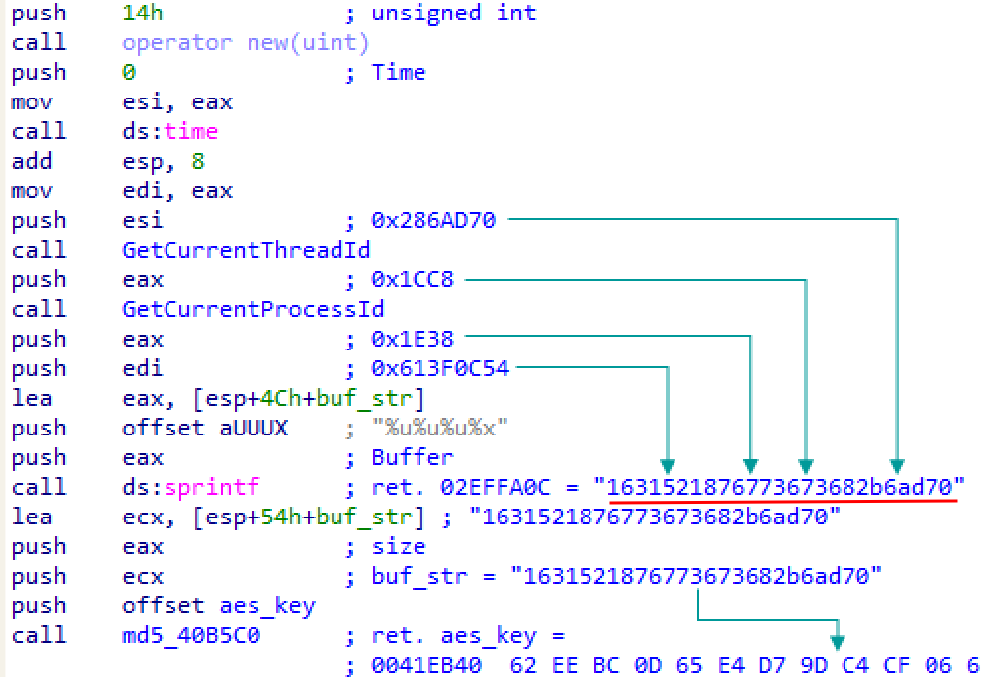
C2 anti-tracking mechanism
This malware sample employs an IP Generation Algorithm to generate a random C2 IP address when the backdoor lacks C2 configuration. The IP produced at random will exist inside particular IP address ranges:
113.62.0.0 - 113.63.255.255 or
111.120.0.0 - 111.123.255.255
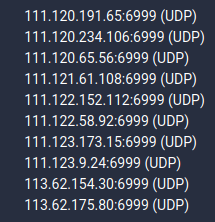
This mechanism will prevent researchers from tracking down the real C2 IP.
Backdoor.Win32.WINDEALER.ZYJA is a variant of the WinDealer malware family. It is a type of backdoor malware that is designed to allow remote attackers to gain unauthorized access to an infected computer system. Once installed, the malware creates a backdoor on the infected system, which allows the attacker to control the system and steal sensitive data.
The Backdoor.Win32.WINDEALER.ZYJA variant is known to be spread through spear-phishing emails that contain malicious attachments. Once the attachment is opened, the malware is installed and begins to communicate with a remote command-and-control server, allowing the attacker to send commands to the infected system and exfiltrate data.
The malware is capable of performing a range of malicious activities, including stealing credentials and sensitive data, taking screenshots, recording keystrokes, and executing arbitrary commands on the infected system. The malware is also capable of bypassing antivirus and other security software, making it difficult to detect and remove.
IOCs
versions
| Malware | version | md5 | sha1 |
|---|---|---|---|
| WinDealer | 18.20.1225 | 76ba5272a17fdab7521ea21a57d23591 | 6b831413932a394bd9fb25e2bbdc06533821378c |
| WinDealer | 18.20.1225 | cc7207f09a6fe41c71626ad4d3f127ce | 84e749c37978f9387e16fab29c7b1b291be93a63 |
domain IPs
113.62.0.0/15 111.120.0.0/14- port
55556/TCP,6999/UDP 221.195.68.71/32122.112.245.55/32
Yara rules (from Malpedia)
rule win_windealer_auto {
meta:
author = "Felix Bilstein - yara-signator at cocacoding dot com"
date = "2023-01-25"
version = "1"
description = "Detects win.windealer."
info = "autogenerated rule brought to you by yara-signator"
tool = "yara-signator v0.6.0"
signator_config = "callsandjumps;datarefs;binvalue"
malpedia_reference = "https://malpedia.caad.fkie.fraunhofer.de/details/win.windealer"
malpedia_rule_date = "20230124"
malpedia_hash = "2ee0eebba83dce3d019a90519f2f972c0fcf9686"
malpedia_version = "20230125"
malpedia_license = "CC BY-SA 4.0"
malpedia_sharing = "TLP:WHITE"
/* DISCLAIMER
* The strings used in this rule have been automatically selected from the
* disassembly of memory dumps and unpacked files, using YARA-Signator.
* The code and documentation is published here:
* https://github.com/fxb-cocacoding/yara-signator
* As Malpedia is used as data source, please note that for a given
* number of families, only single samples are documented.
* This likely impacts the degree of generalization these rules will offer.
* Take the described generation method also into consideration when you
* apply the rules in your use cases and assign them confidence levels.
*/
strings:
$sequence_0 = { 668b91d2070000 8a89d0070000 52 51 }
// n = 4, score = 800
// 668b91d2070000 | mov dx, word ptr [ecx + 0x7d2]
// 8a89d0070000 | mov cl, byte ptr [ecx + 0x7d0]
// 52 | push edx
// 51 | push ecx
$sequence_1 = { ff15???????? 85c0 7407 50 ff15???????? 6a01 }
// n = 6, score = 800
// ff15???????? |
// 85c0 | test eax, eax
// 7407 | je 9
// 50 | push eax
// ff15???????? |
// 6a01 | push 1
$sequence_2 = { 6a01 50 56 e8???????? 83c410 8bc7 }
// n = 6, score = 800
// 6a01 | push 1
// 50 | push eax
// 56 | push esi
// e8???????? |
// 83c410 | add esp, 0x10
// 8bc7 | mov eax, edi
$sequence_3 = { 6a00 ff15???????? 85c0 7407 50 ff15???????? 6a01 }
// n = 7, score = 800
// 6a00 | push 0
// ff15???????? |
// 85c0 | test eax, eax
// 7407 | je 9
// 50 | push eax
// ff15???????? |
// 6a01 | push 1
$sequence_4 = { 6a04 50 6a04 68???????? 68???????? }
// n = 5, score = 800
// 6a04 | push 4
// 50 | push eax
// 6a04 | push 4
// 68???????? |
// 68???????? |
$sequence_5 = { 56 57 68da070000 e8???????? }
// n = 4, score = 800
// 56 | push esi
// 57 | push edi
// 68da070000 | push 0x7da
// e8???????? |
$sequence_6 = { 50 56 e8???????? 83c410 8b4618 }
// n = 5, score = 800
// 50 | push eax
// 56 | push esi
// e8???????? |
// 83c410 | add esp, 0x10
// 8b4618 | mov eax, dword ptr [esi + 0x18]
$sequence_7 = { 8b4d08 668b91d2070000 8a89d0070000 52 51 }
// n = 5, score = 800
// 8b4d08 | mov ecx, dword ptr [ebp + 8]
// 668b91d2070000 | mov dx, word ptr [ecx + 0x7d2]
// 8a89d0070000 | mov cl, byte ptr [ecx + 0x7d0]
// 52 | push edx
// 51 | push ecx
$sequence_8 = { 53 56 57 68da070000 }
// n = 4, score = 800
// 53 | push ebx
// 56 | push esi
// 57 | push edi
// 68da070000 | push 0x7da
$sequence_9 = { 8b4d08 668b91d2070000 8a89d0070000 52 }
// n = 4, score = 800
// 8b4d08 | mov ecx, dword ptr [ebp + 8]
// 668b91d2070000 | mov dx, word ptr [ecx + 0x7d2]
// 8a89d0070000 | mov cl, byte ptr [ecx + 0x7d0]
// 52 | push edx
condition:
7 of them and filesize < 770048
}
By Cyber Threat Hunters from MSSPLab:
Thanks for your time happy hacking and good bye!
All drawings and screenshots are MSSPLab’s